For those looking to get a really granular look inside DNS queries, or really any network traffic, the tool of choice is tcpdump.
Short of looking at the 1s and 0s that are transmitted, tcpdump in concert with a tool like Wireshark can take a snapshot of network traffic during a specified window of time for detailed analysis. This comes in handy when trying to determine who’s to blame for slow network performance, whether or not a request is even getting to the place it’s supposed to go, or if DNS packets are being malformed upon request.
Basic tcpdump
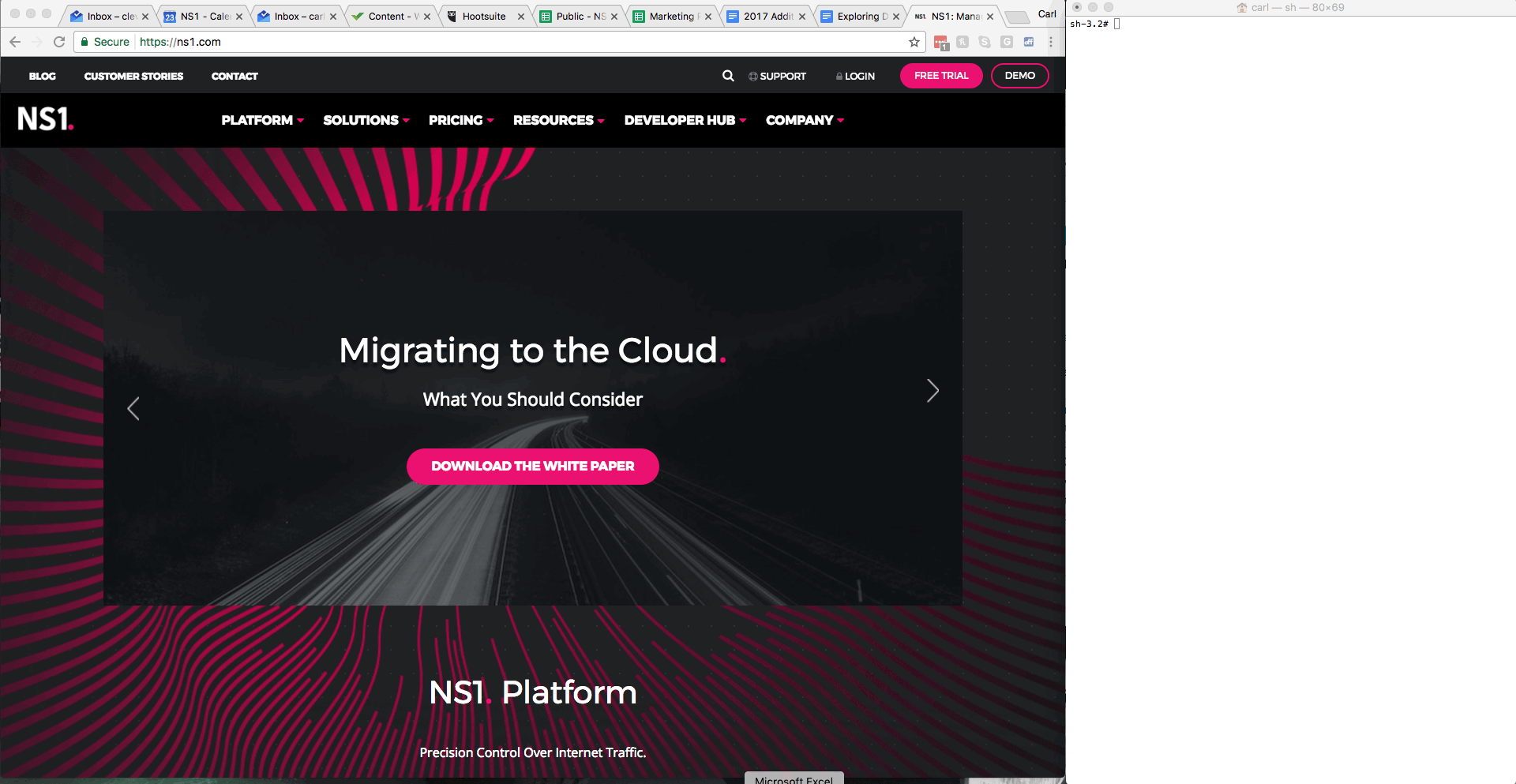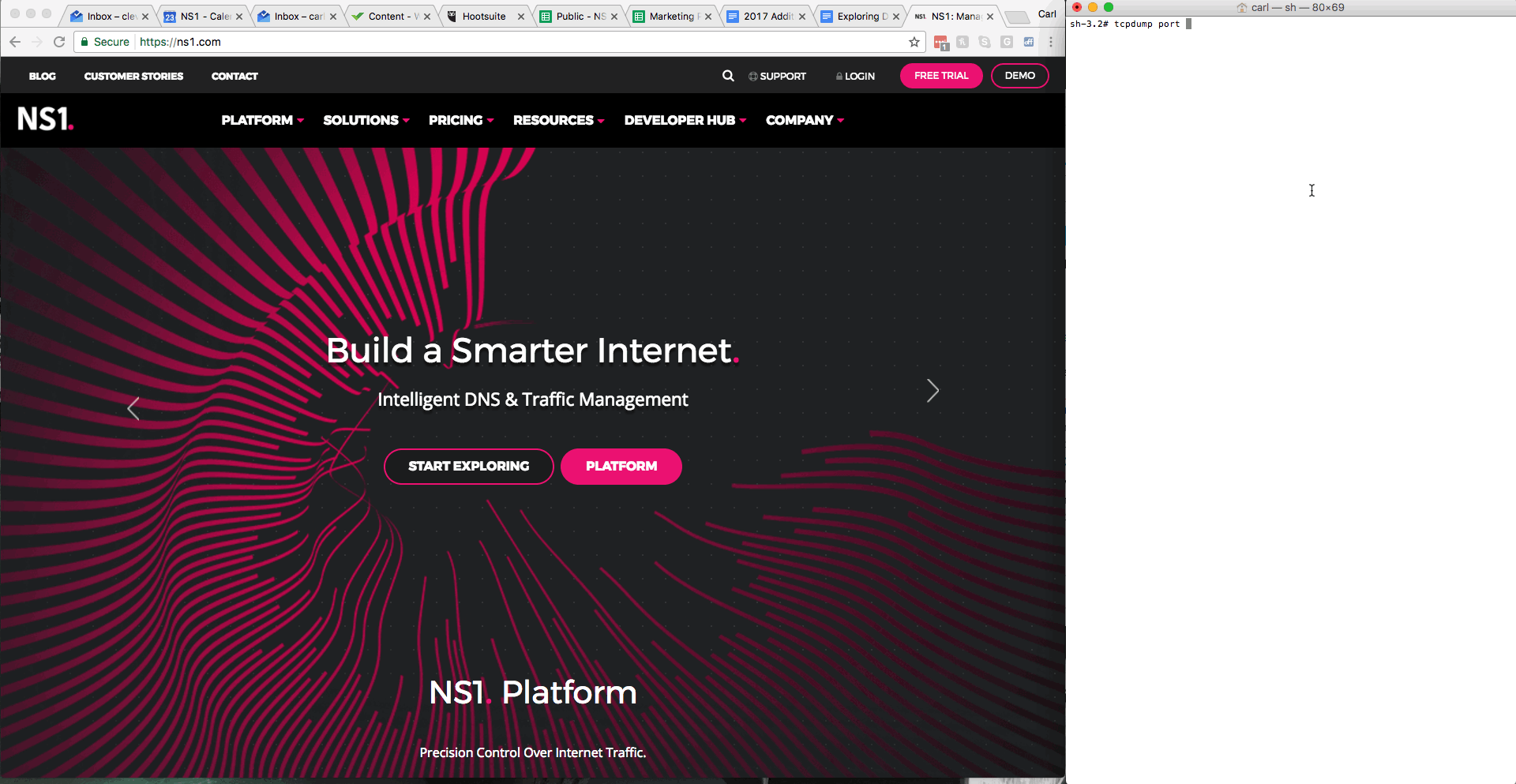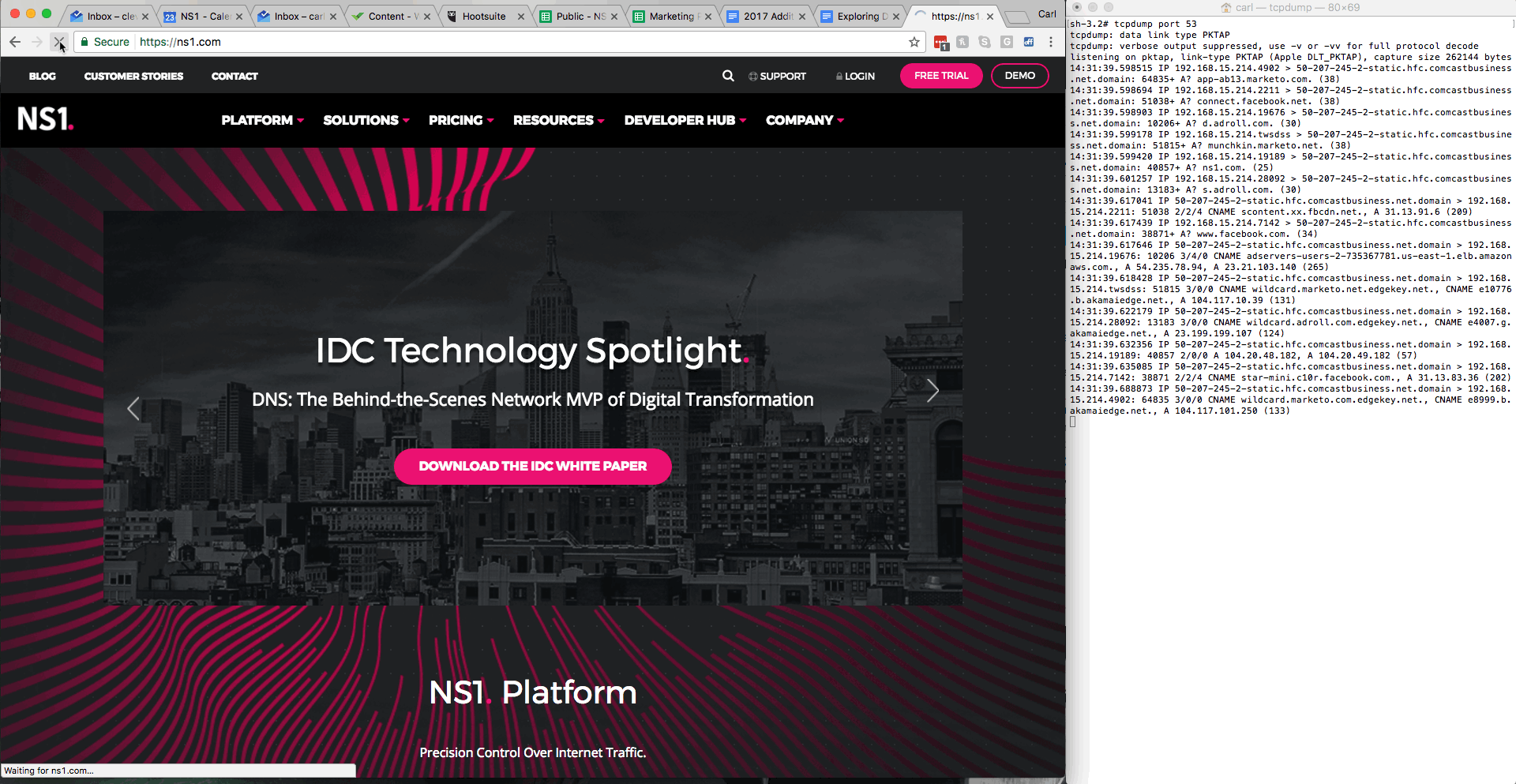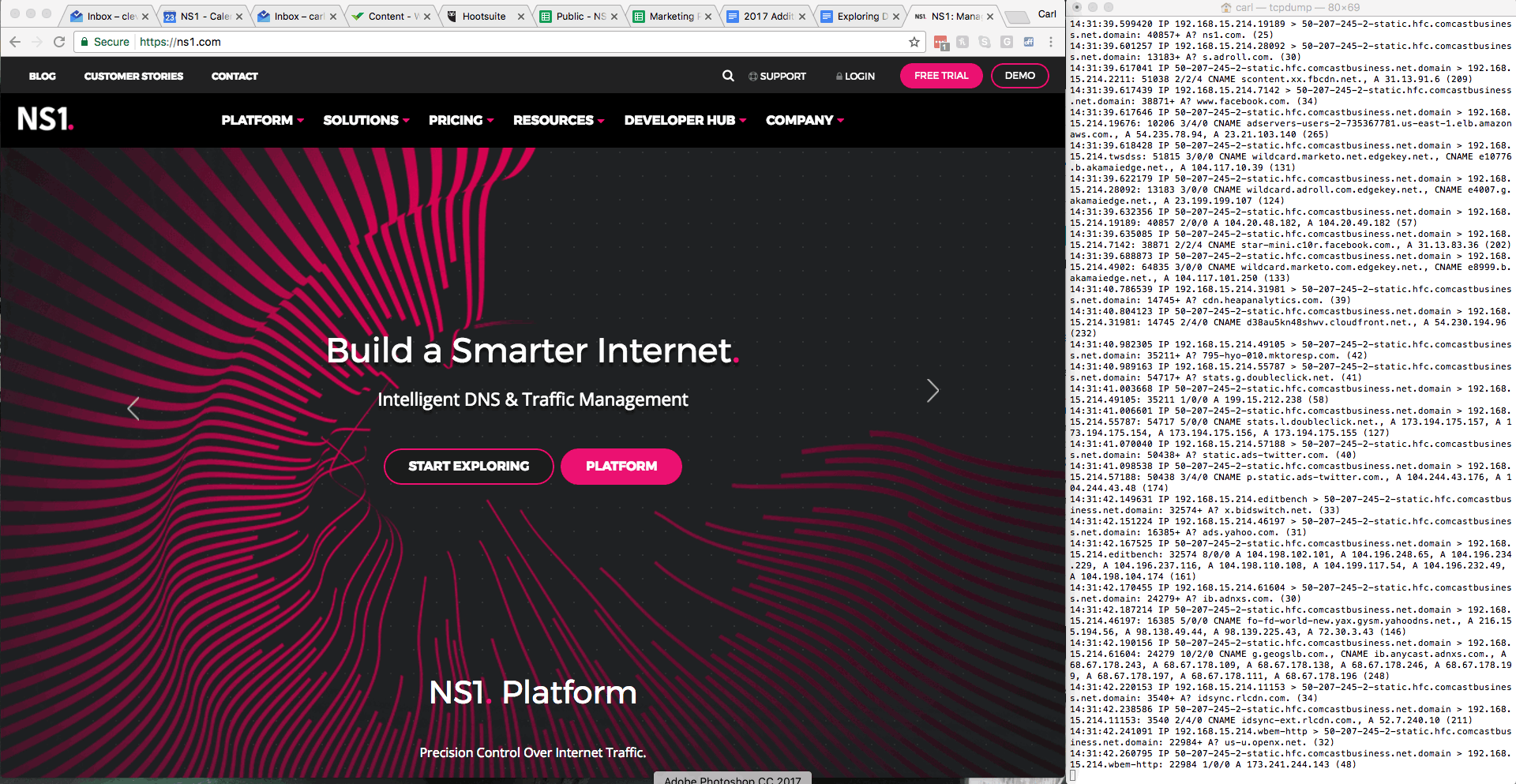
In its most basic form, tcpdump is configured in this example to show all traffic on Port 53 - the place where all this DNS magic takes place. As you can see in the example above, there’s a Chrome window with a nifty looking website, and a terminal screen that’s logged in as root. Sudo is required to use tcpdump in most cases.
$ tcpdump port 53
The tcpdump utility is now running, so once some DNS queries start happening, the screen lights up with relevant information. In this example, we kicked this off by refreshing the browser screen. Press CTRL+C to stop the utility.
Adding Wireshark To Help Analyze The Data
As we saw in the previous example, basic tcpdump will do exactly as its name implies - dumps data onto the screen. With a quick modifier on the command, the same data along with even more granular information, can be piped into a packet capture (.pcap) file.
$ tcpdump port 53 -w yourfilenamehere.pcap
Wireshark is an open source utility that is available for a wide array of computing platforms that allows detailed analysis of packet capture files. Opening a packet capture file in a traditional text editor will show you a bunch of unintelligible gibberish, so having a tool like Wireshark is paramount to your success.

This example of a packet capture shows all of the embedded information that is normally not visible to the human eye. The top section of the window shows a detailed timeline of each activity in the file, starting at 0.0000 which represents the first transaction recorded in the file. The information across the columns is what one would typically see in a packet capture done through tcpdump in a terminal screen, albeit a touch more organized and with the ability to adjust the column attributes.
The second section is where things start to get a lot more interesting, as all of the metadata about the transaction is broken out into specific categories. While I could detail everything that you’ll see in there, by the time I’d have written it all, you could have gone and explored as well! Lastly, the third section is the hexadecimal breakout of the packet capture.
When In Doubt, tcpdump!
It’s almost hard to believe that in this day and age that such a powerful tool is available for free, across so many different operating systems. With time and experience, tcpdump will quickly become an indispensable and essential part of your toolbox. Far beyond the fun Managed DNS stuff we’re doing here at NS1 on Port 53, there’s a whole world of information and data that can be analyzed with tcpdump.